2020.04.10
1. ClusterIP
- A ClusterIP service is the default Kubernetes service. It gives you a service inside your cluster that other apps inside your cluster can access. There is no external access.

$ k proxy --port=8080 &
[1] 893
ysjeon71_kubeflow2@cs-6000-devshell-vm-92bccb22-ff7a-491b-99a2-c333678d033d:~/exam-tfserving$ Starting to serve on 127.0.0.1:8080
The service’s proxy URL:
http://kubernetes_master_address/api/v1/namespaces/namespace_name/services/[https:]service_name[:port_name]/proxy
$ curl -X POST -d @input.json http://localhost:8080/api/v1/namespaces/kubeflow/services/mnist-service:8500/proxy/v1/models/mnist:predict
…
$
2. NodePort
- A NodePort service is the most primitive way to get external traffic directly to your service. NodePort, as the name implies, opens a specific port on all the Nodes (the VMs), and any traffic that is sent to this port is forwarded to the service.


$ k get svc kubia-nodeport
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubia-nodeport NodePort 10.63.248.71 <none> 80:30123/TCP 2m43s
$ k describe svc kubia-nodeport
…
Type: NodePort
IP: 10.63.248.71
Port: <unset> 80/TCP
TargetPort: 8080/TCP
NodePort: <unset> 30123/TCP
Endpoints: 10.60.4.10:8080,10.60.4.5:8080,10.60.4.6:8080 + 3 more...
…
$ k get nodes -o wide
NAME STATUS ROLES AGE VERSION INTERNAL-IP EXTERNAL-IP OS-IMAGE KERNEL-VERSION CONTAINER-RUNTIME
gke-my-kubeflow-my-kubeflow-cpu-pool--5b5549e0-2kfh Ready <none> 97m v1.14.10-gke.27 10.142.0.11 35.227.87.160 Container-Optimized OS from Google 4.14.138+ docker://18.9.7
gke-my-kubeflow-my-kubeflow-cpu-pool--5b5549e0-ntcs Ready <none> 31m v1.14.10-gke.27 10.142.0.15 35.196.119.78 Container-Optimized OS from Google 4.14.138+ docker://18.9.7
$
$ k exec kubia-5dfcbbfcff-9khml -- curl -s 10.142.0.11:30123
This is v1 running in pod kubia-5dfcbbfcff-9mwv8
$
$ gcloud compute firewall-rules create kubia-np-rule --allow=tcp:30123
Creating firewall...⠶Created [https://www.googleapis.com/compute/v1/projects/my-kubeflow-271310/global/firewalls/kubia-np-rule].
Creating firewall...done.
$ gcloud compute firewall-rules list --filter=kubia-np-rule
NAME NETWORK DIRECTION PRIORITY ALLOW DENY DISABLED
kubia-np-rule default INGRESS 1000 tcp:30123 False
$ curl 35.227.87.160:30123
This is v1 running in pod kubia-5dfcbbfcff-z5dgt
$
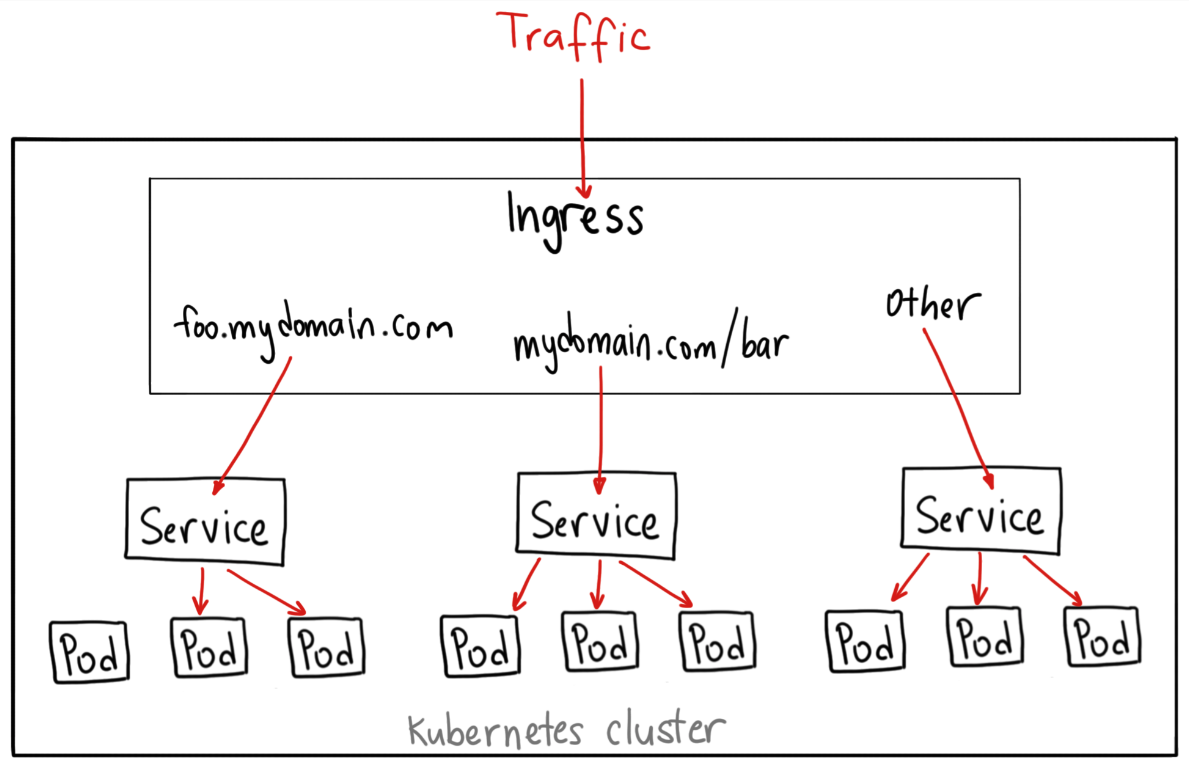
3. Ingress
- 참고: https://blog.naver.com/alice_k106/221502890249
- Unlike all the above examples, Ingress is actually NOT a type of service. Instead, it sits in front of multiple services and act as a “smart router” or entrypoint into your cluster.
There are many types of Ingress controllers, from the Google Cloud Load Balancer, Nginx, Contour, Istio, and more.

$ k get svc kubia-nodeport
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubia-nodeport NodePort 10.63.248.71 <none> 80:30123/TCP 23m
$ k get ingress
NAME HOSTS ADDRESS PORTS AGE
kubia kubia.example.com 35.186.241.29 80 5m3s
$ k describe ingress kubia
…
Rules:
Host Path Backends
---- ---- --------
kubia.example.com
/ kubia-nodeport:80 (10.60.4.10:8080,10.60.4.5:8080,10.60.4.6:8080 + 3 more...)
…
$ curl -H "Host:kubia.example.com" http://35.186.241.29
This is v1 running in pod kubia-5dfcbbfcff-z5dgt
$
'Kubernetes > Management' 카테고리의 다른 글
| Istio 1.5 구성 (0) | 2021.09.23 |
|---|---|
| Cert-manager with LetsEncrypt (HTTP challenge) (0) | 2021.09.23 |
| K8s 잡학다식 (0) | 2021.09.23 |
| Cert-manager with LetsEncrypt (DNS challenge) (1) | 2021.09.23 |
| Crobjob (0) | 2021.09.23 |



댓글